In October 2022, Australia experienced yet another significant data breach, this time affecting Medibank, one of the larger and more trusted health insurance companies in the country.
The system-wide breach involves up to 4 million health profiles including information such as names, addresses, dates of birth, Medicare numbers, phone numbers, and medical claims data, like details on diagnoses, treatments, the location of medical services, and possibly credit card information.
An anonymous contact with insider knowledge who has spoken to the Guardian advised the consensus so far, though this is an evolving situation, is that the criminals gained entry via a set of stolen high-level Medibank credentials that they’d purchased off of a Russian-speaking internet black market. Once inside it's believed they carried out thorough intelligence gathering for an unknown amount of time, learning all they could about Medibank’s network.
This process involves things like running network scans to see what’s going on in the business, reviewing documentation, assessing business security capabilities, and looking for valuable servers and applications holding sensitive data within the company.
It’s believed the attackers went to work laying 2 back doors to act as a spare set of keys to the Medibank network should their stolen credentials stop working. Then, armed with a satisfactory understanding of Medibank’s environment, they built a custom tool that gave them the ability to quickly collect large amounts of sensitive data from a range of Medibank’s systems. The company was unable to stop the intruders in time before they successfully trafficked 200GB of Medibank data outside the system.
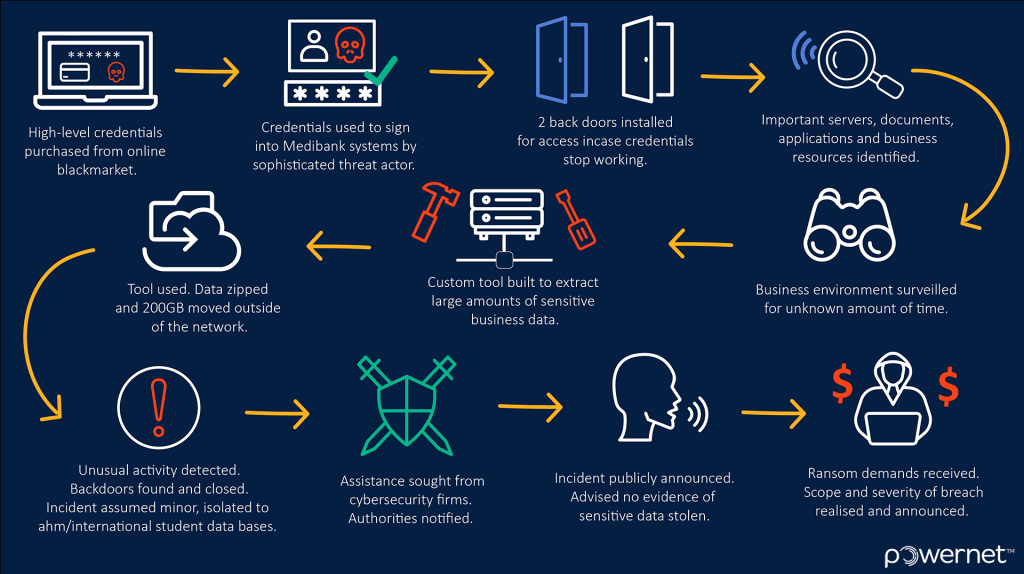
Medibank discovered the unusual activity on their network on October 12 and sought assistance from renowned cyber security companies CyberCX and CrowdStrike. The following day, it was announced that due to a "cyber incident" contained to the AHM system, and the international student division, the systems would be shut down temporarily.
Once service was restored Medibank informed customers and authorities that there was no evidence of any unauthorised access to sensitive customer data and that the incident was under investigation. It would be another week before Medibank received the first extortion demands from the criminals responsible, and the full extent of precisely how extensive and severe the breach had been, would be made public.
"Our investigation has now established that this criminal has accessed all our private health insurance customers' personal data and significant amounts of their health claims data," David Koczkar CEO of Medibank said Wednesday 26th. "I apologise unreservedly to our customers. This is a terrible crime – this is a crime designed to cause maximum harm to the most vulnerable members of our community."
Fortunately for Medibank, security personnel were able to shut the criminals out before they could move on to the next stage, which the Australian Signals Directorate warned based on online criminal comments they were seeing, would be the deployment of ransomware.
The threat of extortion remains on the date of this publication though, as the cybercriminals have promised Medibank they’d go after the top 1000 most prominent Australians whose health information they have if payment isn’t made, and that will be just the beginning.
Medibank is now grappling with the immense ethical dilemma of determining whether or not they should pay the ransom. While it is not against the law for corporations to pay a ransom, it is heavily discouraged by Government, and doing so may put companies at odds with laws that prohibit payment to known criminal entities.
On the one hand, it is well documented that many Australian businesses have paid ransoms with the expectation that the criminals will honor their word, return or delete the data in their possession, and leave the company alone.
On the other hand, it's widely known that there’s no honor among thieves, and businesses run the risk of incentivising such crime without any assurance that they won't still be subjected to further extortion or have their data leaked anyway. It’s a position that no business owner would envy and for now, Medibank remains tight-lipped about what they’re going to do.
What can you do if you’ve been affected by this most recent breach or any of the recent breaches.
- Sign up for credit monitoring services from an agency like Equifax, for visibility and protection on any unauthorised lines of credit attempting to be opened in your name. You can read our blog post about the Optus breach for further information on how to do this.
- Enquire about receiving a Medicare replacement number.
- Take stock of your sensitive accounts and wherever possible enable Multifactor Authentication (MFA).
- Review your passwords that protect your accounts, and reset any weak or reused passwords. Do you have an easy way to manage this? If the answer is no, consider setting up a password manager like KeeperSecurtiy or Bitwarden to help set and remember complex passwords for you.
- Remain highly vigilant about scams and unsolicited calls, emails, and text messages. Remember a lot of information is available now, scammers are quoting real information during their scams when they contact people. If anyone calls claiming to be from a service known to you ask for a case number to quote and call them back on their official line from their official website.
- Lock down your social media. Scammers have been known to collect photos, information about friends and family, and information about you on social media prior to stealing your identity or trying to scam you. It's important we don’t hand over the information that we do control to anyone who’d be willing to use it against us.
How to Unsend an Email in Outlook “Have you ever experienced that sinking feeling in your stomach after accidentally sending […]
Read moreWe all spend a great deal of time in our internet browser, searching, googling, so it makes sense to not […]
Read moreOn a busy IT helpdesk, no one day is the same. There are a multitude of different reasons clients call […]
Read more
























