Recently, one of our cybersecurity gurus went to a few op shops around Melbourne to see what digital items they could find. There were quite a number of USB sticks, so they purchased them and took on the task of finding out what they could about the USB stick's past owners.
Deleting data from a USB stick or hard drive the normal way (file>delete), does not remove the files as we think it does. What we do when we just delete files from a USB is we remove the files from sight, but they're still there, lurking, waiting to be overwritten, or recovered by the curious with nothing better to do on the weekend.
Reading this may prompt you to smash all of your old USBs and hard drives with a hammer or wipe them properly after use, using a wiper like DBAN - Wiper. Either way, this task made for an interesting Sunday afternoon.
These were all the USB's we could find in our travels. Most of them were bundled up in a big bag for $4.
- An old laptop with Kali Linux- and a piece of software called PhotoRec.
- PhotoRec is an open source program available for many Linux distributions and is a companion program to Testdisk - another file recovery program. There are also plenty of free data recovery tools compatible with Windows like Autopsy Browser or Recuva.
- 20 seemingly blank USBs all with a mysterious past.
Now, plugging mystery USBs into your personal or work computer is a terrible idea - please don't do that. When analysing an unknown device we always want to assume it's riddled with Malware.
The easiest way to check these out is to use an old laptop, that's not connected to anything on your home or work network. A computer that you are happy to wipe or reset to factory settings after exploring and has been set up with the required tools. You can use VMs and specially made Sandboxes but we won't go into that here.
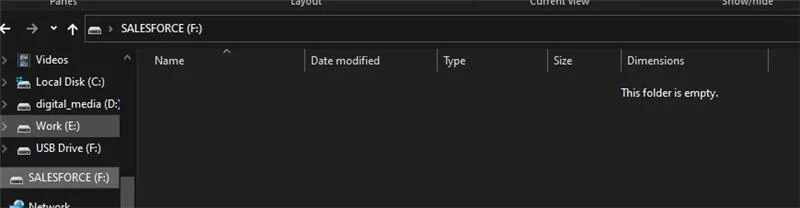
So, the USB was plugged into Kali and scanned. Then, for the purposes of showing you what it looks like in a Microsoft Windows computer, a Windows VM was created. The USB stick appears completely blank.
We then installed PhotoRec (detailed instructions on how to use this program properly can be found here).
The commands we entered into the computer:
$ sudo apt update
$ sudo apt install testdisk -y
And Opened it up
$ sudo photorec
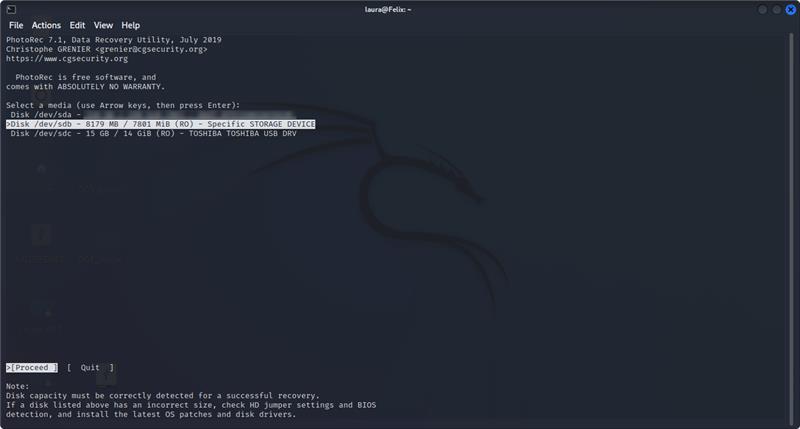
Specific Storage Device is the one I want, so I select it with the arrow keys and hit Enter on the keyboard.
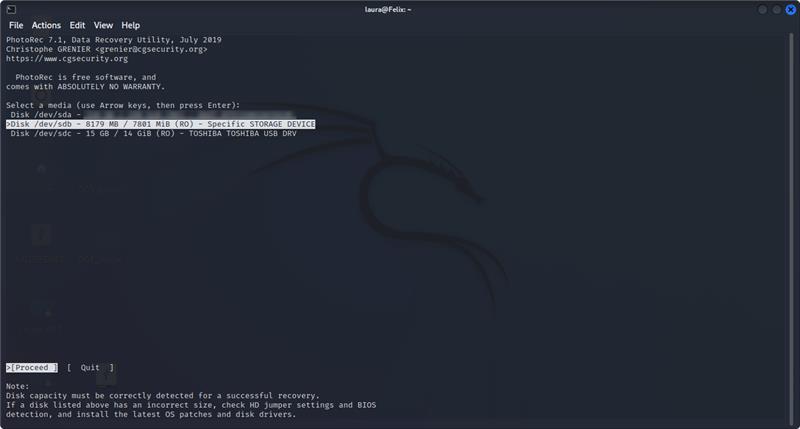
Next, I selected the Salesforce partition.
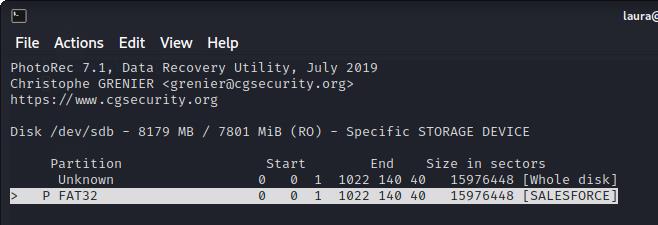
Then I selected the 'FAT file system' to tell the program what type of file system the USB uses.
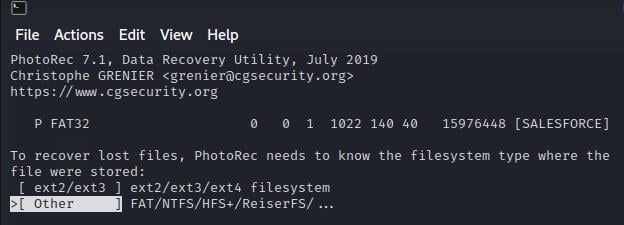
I then selected to analyse the free space on the USB, as the USB appeared blank. So, anything on the device should be marked as free space.
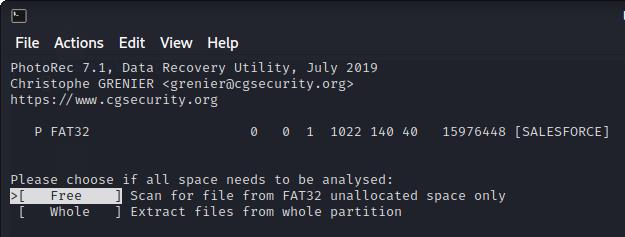
Then I specified in PhotoRec where to put the recovered files on my Desktop.
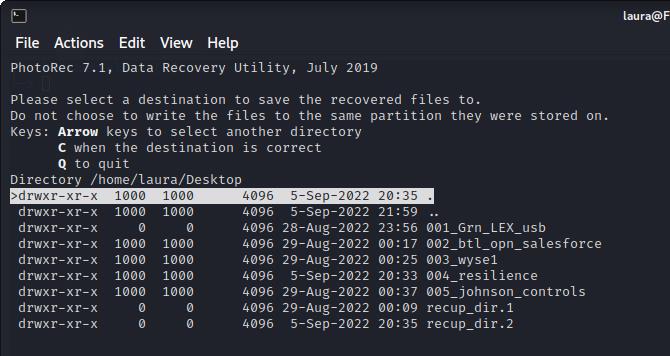
And that's it, PhotoRec began analysing and extracting the data it could find on the USB sticks that appeared to be blank.
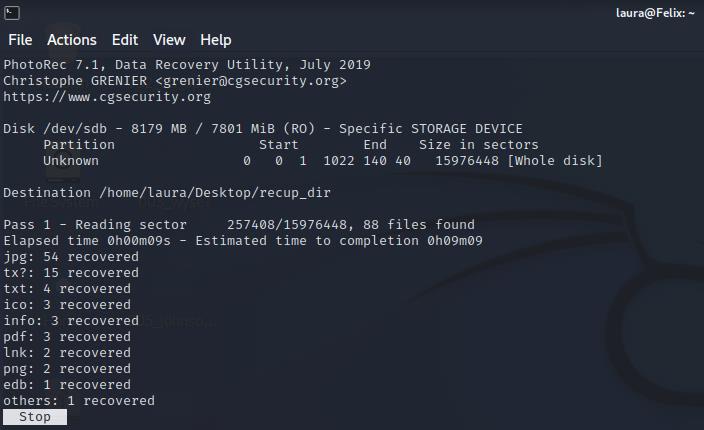
This same process was repeated about 20 times across 20 USB sticks.
- legal documents
- Sensitive Work/Corporate files
- Family Photos
- Personally Identifiable Information
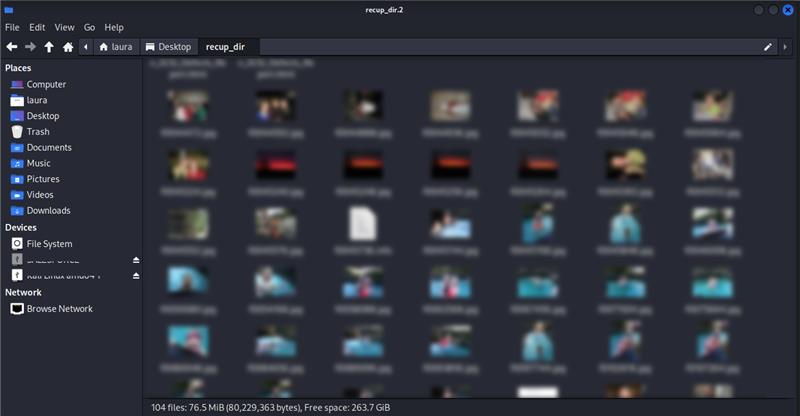
From the information on the USBs the person's full name, home address, family names, workplace, lawyer and work role information were able to be recovered and confirmed.
It's easy to see how this data could be used maliciously, there was certainly enough there for identity theft.
This is one of the reasons we're so pro-encryption at Powernet for USBs, and hard drives. This is why we made it mandatory for our business, that only encrypted USBs and hard drives can be used on work computers.
On an unencrypted device, the files are completely exposed. Even if you delete sensitive client files, personal documents and photos, they can easily be recovered if that USB is lost or recycled.
The process that was used today was a fairly basic one. There are complex forensic tools available that can reconstruct data and extra information from more complex setups. Please note, that this was an exercise in education and the information will not be used and has been properly disposed of.
1. Encrypt them, here is an article on how to do this using Bitlocker for Windows: https://tech.wayne.edu/kb/security/computer-device-security/261865.
Remember to save the encryption key in your password manager so you don't lose it or you'll be locked out.
2. Having trouble with USB encryption? Get in touch with our helpdesk, they'd love to help.
3. Destroy USB sticks or dispose of them properly. If you're unsure how, our team can help.
If you want to remove that stubborn blank page at the end of your report or delete a page containing […]
Read moreHow to Unsend an Email in Outlook “Have you ever experienced that sinking feeling in your stomach after accidentally sending […]
Read moreWe all spend a great deal of time in our internet browser, searching, googling, so it makes sense to not […]
Read more
























