Sadly, during any wide-spread news event, there will usually be an increase in malicious activity relating to it. We have seen fake emails, text messages and calls pretending to be helping during the COVID-19 pandemic. Unfortunately, community stress and panic provide an opportune time for cyber criminals to attack.
Since early March 2020, there has been a significant increase in COVID-19 themed malicious cyber activity across Australia. The Australian Competition and Consumer Commission’s Scamwatch has received more than 100 reports of scams about COVID-19 in the last three months, and the volumes continue to rise. Between 10 and 26 March, the ACSC has received over 45 cybercrime and cyber security incident reports from individuals and businesses, all related to COVID-19 themed scam and phishing activity. The true extent of this malicious activity is likely to be much higher, as these numbers only represent those cases reported to the ACSC and ACCC.
There are many things you can do to protect yourself, we we believe empowering individuals with information through education is the best protection. How can you ensure the information you are sharing with your team is accurate and doesn't leave any gaps? The government's Stay Smart Online site is a great place to start for alerts and general cyber security advice.
Security is an essential part of any businesses Technology Strategy and is something we have always focused on, throughout our 25 years of operation. We have a team who are focused on security and ensuring our clients receive the best advice on how to protect themselves.
If you'd like to get our experts in, we offer cyber security training . We can also provide you with content or some tips and tricks specific to your business on what to look out for.
For now, here is some advice on staying safe during this time:
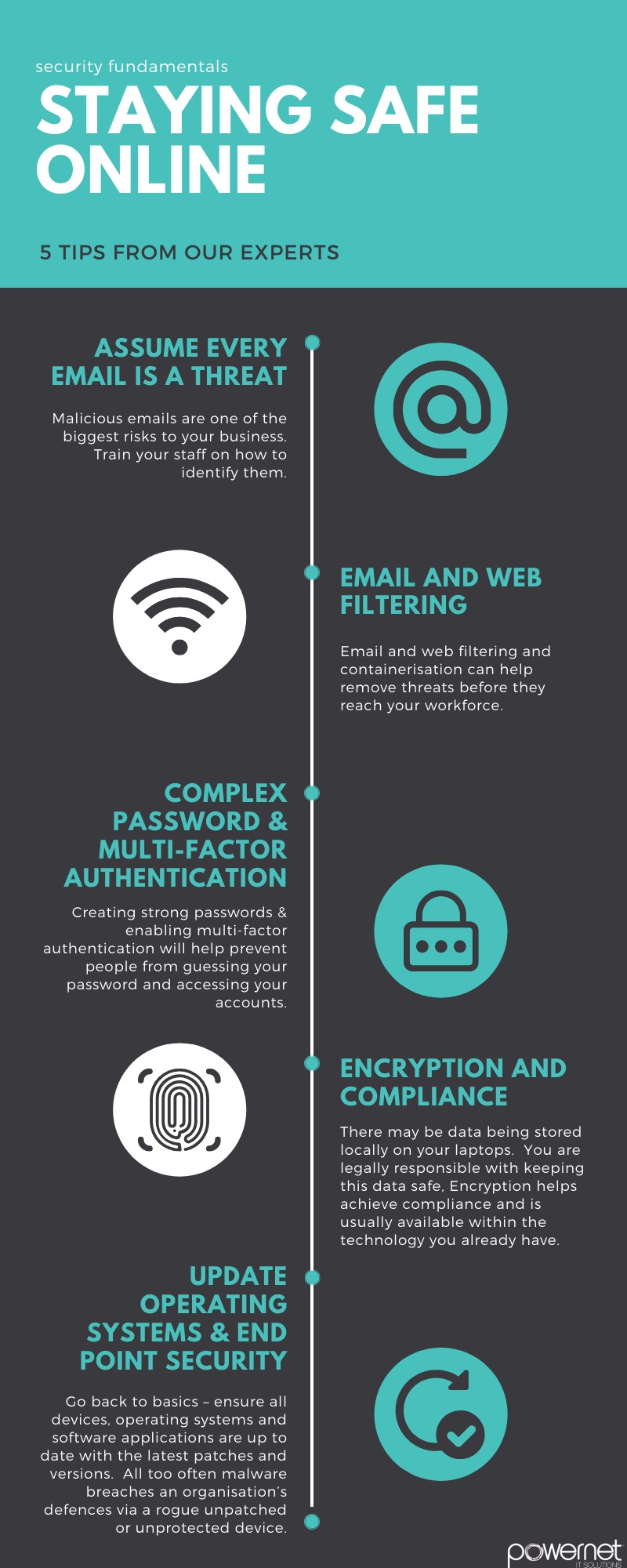
Home working will likely lead to a big increase in email as people can no longer speak to colleagues in person. Malicious cyber actors are spreading phishing emails and text messages that pretend to be from reputable organisations, seeking to deceive recipients into visiting websites that host computer viruses or malware designed to steal their personal information. To increase the appearance of legitimacy, these phishing emails are sent from addresses that closely resemble the official organisations or entities, often adopting the official message format and including well-known branding and logos.
1. Before opening an email, consider who is sending it to you and what they’re asking you to do. If you are unsure, call the organisation or individual you suspect the suspicious message is from, using contact details from a verified website or other trusted source.
2. Do not open attachments or click on links in unsolicited emails or messages.
3. Do not provide personal information to unverified sources and never provide remote access to your computer.
4. Remember that reputable organisations locally and overseas - including banks, government departments, Amazon, PayPal, Google, Apple and Facebook - will not call or email to verify or update your personal information.
Email filtering is the first step in removing of the majority of threats before they reach you and your team. Web filtering helps protect your team navigating threats online, malicious websites can look very convincing and can trick even the savviest of folk. Web filtering can flag and block these websites before they become an issue.
Creating strong passwords across your user accounts and applications, combined with multi-factor authentication, will help prevent people who guess your password from gaining access to your accounts. Most of the time multi factor authentication tools are available within your existing suite of technology, it is an inexpensive and very effective mitigation tool!
Go back to basics – ensure all devices, operating systems and software applications are up to date with the latest patches and versions. All too often malware breaches an organisation’s defenses via a rogue unpatched or unprotected device.
Anti-virus is no longer enough. There are many cost effective solutions to upgrade your anti-virus to include other modern measures that assist with protection against vulnerabilities on your own desktop or notebook. Ensure that it is up to date and correctly licensed.
Depending on your remote working setup, there may be more data being stored locally on your desktop or notebook. You are legally responsible with keeping this data safe, and in situations of the loss of this data into another person’s hands (lost/stolen), you may be required to register this loss as a data breach. Breaches can cause damage to your business, reputation as well as all your clients and the individuals concerned. Most devices include native encryption tools such as BitLocker or FireVault – be sure to use them. This is another inexpensive and effective way to add protection.
There is a lot of technology available to help mitigate the risks and flag suspicious activity before they hurt you or your business. Mitigating risk, education and reducing your exposure is the most effective and inexpensive way to protect your business.
We can help you choose the right technology to support your business, during this time we are offering free phone consultations to help businesses protect themselves. If any part of this article was of interest to you or if you would like advice on how to secure your business please get in touch and ask to speak with our sales team, we are here to help!
If you want to remove that stubborn blank page at the end of your report or delete a page containing […]
Read moreHow to Unsend an Email in Outlook “Have you ever experienced that sinking feeling in your stomach after accidentally sending […]
Read moreWe all spend a great deal of time in our internet browser, searching, googling, so it makes sense to not […]
Read more
























